In this fast-paced digital world, technological advances have given us many substitutes for previously manual operations. Consequently, it’s now impossible to imagine getting through the day without our mobile phones. From waking up to the sound of an alarm clock, to setting up client meetings, to participating in online conferences, mobile phones have become an integral part of our daily existence.
Based on recent trends, it’s easy to see why mobile devices are starting to shape the different systems we use not only to connect with people but to manage our lives and businesses. This leads us to the unique innovation in mobile technology—mobile access control. With mobile access control, we are better disposed to access, view, and manage critical events by simply installing security software on mobile phones. This technology is rapidly emerging as a viable alternative to physical access systems, ushering in a new era of enhanced access management.
What is a mobile access control system? #
Mobile access control takes smartphones, tablets, and wearable electronic devices and allows them to function as a user’s credentials to enter offices or other business facilities. As more and more employers encourage the Bring Your Own Device (BYOD) trend, app access control is becoming a great tool to add an extra layer of security to any organization. Now, electronic devices even enable biometric authentication without the need to invest in expensive biometric readers.
How does mobile access control work? #
In the majority of cases, mobile access control is powered by Bluetooth, allowing phones to communicate with a reader placed on a door. These days, there’s no need for pairing devices manually. For instance, Bluetooth Low Energy (BLE) technology will take care of that often frustrating process. A secure Bluetooth connection can be established from a few feet away, giving Bluetooth access a noticeable edge over traditional RFID card technologies with an average read range of about an inch. Thanks to mobile access control, there’s also no longer a need for access control cards.
NFC (near-field communication) technology is often applied in mobile access control. You have probably heard of it as it is commonly used for payment applications. Similar to Bluetooth, a phone gets connected to a reader. The drawback of NFC, though, is that it doesn’t let you connect from a distance. Its range is only a few inches.
Introduction to smartphone access control systems #
Mobile access control systems offer access to secured buildings and rooms with just a couple of taps on mobile devices, including smartphones, tablets, and wearable tech. Such systems provide building and office managers with a cost-effective solution for managing identification credentials. The ease and convenience make mobile access controls a promising alternative to physical cards.
The world of mobile access control #
There are a variety of access control systems available on the market, from systems operated by local servers to personalized, cloud-based access control systems with numerous high-end features. Although local systems only require a one-time investment, the smartphone access included with cloud-based systems makes them a much more economical choice for long-term applications. The major types of smartphone door access control systems are IP systems, control panel systems, and mobile access credentials. The following sections offer a brief insight into these systems.
IP systems #
For start-ups or small companies working with only a handful of suppliers and clients, managing contacts is relatively easy. However, bigger companies dealing with thousands of clients across the globe might find working with local systems a hassle. In comparison, cloud-based IP systems are specially designed for large businesses while also enabling easy access and data management in the cloud.
Control panel systems #
Control panel systems have a number of applications. They are often installed locally, allowing users to manage credentials and generate reports. One advantage of these computerized systems, installed directly at workspaces, is that they can be integrated into the security system, helping to ensure the safety of employees and clients.
Mobile access credentials #
For many reputable institutions, controlling access to office spaces can be a big concern. Mobile access credentials can be especially beneficial to companies struggling with this, as they enable operators to keep track of employees’ entry and exit activities.
Mobile access credentials also provide a secure way for license key holders to access particular locations within a building. Some other common advantages of these systems include ease of operation, improved security, and remote office management capabilities. Mobile-enabled employees are granted access to a specific physical location with just a few clicks on their phones. Plus, access is generally managed in the cloud, allowing an administrator to easily grant and revoke mobile credentials.
With more and more companies of all sizes choosing to install mobile access control systems, they have become an indispensable part of security in the corporate world. It’s not surprising that so many organizations are switching to mobile access control instead of printed identity cards and physical documents, as mobile access control offers a more convenient experience for both workers and administrators.
Understanding the differences between a regular access control system and a mobile-based access system #
Access control has only one purpose: It grants and revokes access to resources or locations within an organization’s space. Access control can be broadly classified into two categories, physical access and smartphone access. While the former can restrict access to certain rooms, areas, and valuable assets, the latter can also limit access to computer networks, digital files, and classified data. In this ever-growing digital world, it is becoming increasingly crucial for businesses to shield discreet information, making smartphone access systems the right choice for many organizations.

Physical access control #
Physical access control regulates the entry and exit of employees to a particular space. Some common examples of physical access control systems are:
- Fob controlled gates
- RFID doors
- Password Protected Systems
Although physical access control can be a reliable option, proper access control measures must be taken to ensure an effortless transition from one space to another.
Cloud-based mobile access control #
Mobile access control, on the other hand, consists of identification, authentication, and authorization systems. This type of access control is very different from physical access control, which uses badges, keys, and other physical tokens to provide access to a particular location or asset. Businesses and other institutions use a wide array of mobile access control systems, from password-protected programs to biometric security systems. With mobile access control systems, all access permissions are regulated in the cloud by specialized security agents.
The technology behind mobile access control systems #
Mobile access control systems come with a variety of technologies to enable smart access to restricted spaces and data. The following section discusses the major technologies used in cloud-based mobile access control systems.
Bluetooth Low Energy (BLE) #
Generally, mobile access control manufacturers rely on Bluetooth to enable workers to communicate with a remote reader through their smartphone. Bluetooth Low Energy, or BLE, allows access readers to communicate with users’ devices without the hassle of manual pairing. Bluetooth technology also provides sufficient bidirectional bandwidth to power a secure connection, allowing workers’ devices to communicate with an office’s remote reader from a few feet away.
Near Field Communication (NFC) #
Apart from Bluetooth, other technologies like Near Field Communication, or NFC, can be used in mobile access control. NFC allows for communication between a reader or lock and a mobile device.

Mobile access control technology overview #
Some popular technologies used in these control systems include:
- Transmission standards, including Bluetooth, NFC, and RFID
- IT equipment, including Internet Switches, Cat6-cable, and PoE in Access Control
- Technologies, including Wireless Access Control, PACS, and Internet of Things (IoT)
Some of these control systems also come with QR-code detection capabilities. In such cases, the reader is equipped with a QR-code scanner to read employees’ code. This technology has widespread popularity because of the abundant flexibility it gives to users. Today, almost all major platforms rely on a cloud-based service to generate personalized security numbers. With a QR code reader, the reader or lock is provided with this specific number to enable access to specific locations or assets.
The benchmarks of the best mobile access systems #
With the growing popularity of mobile access control, the market is booming with cloud-based logical access control systems. With so much to choose from, it can be difficult to select a reliable system that will provide the best mobile access solution for your organization.
What are the benchmarks of a standard mobile access system? There are some essential criteria that can help to distinguish a good solution from a bad one. Here are the features that all good access control systems should have:
- Credential options
- Access reporting solutions
- Visitor management options
- Provisions for time tracking
- Customer support
- Self-service documentation
Before installing any high-end security system, it is always recommended to carry out thorough research to ensure you’re choosing the best solution for you.
How do users deploy a mobile access system? #
With 6.92 billion smartphone users worldwide in 2023, the use of phones as security keys is obviously a convenient alternative to physical badges. Plus, mobile access systems can be installed in all major commercial sectors, from small start-ups to large organizations. Here are some popular reasons for incorporating a mobile access system into an organization’s security system.
- Smartphone-enabled systems can be easily used in office buildings for ordering, distributing, and managing user credentials.
- With mobile access control, providing mobile credentials to the workforce is usually done through email. Generally, the identification number or code is securely sent to a user’s smartphone, granting them access to specific locations and IT assets.
- Administrative bodies or security professionals can use batch uploads via CSV or Excel files when adding users or use SSO and SCIM integrations for automated provisioning.
- With these systems, employees don’t need to check in to remote locations by flashing temporary physical tokens, as access is regulated virtually in the cloud, ensuring an outstanding user experience.
For these reasons and more, the abundant flexibility and advanced security of mobile access control signals a revolutionary leap in security management.
The benefits of mobile access control #
By implementing mobile technology, organizations benefit through the convenience of use, effectiveness, and cost savings. All of the above features also ensure a high level of security.
Because people are so used to using their smartphones to carry out everyday activities already, expanding the use of mobile devices to access control adds an extra layer of convenience. There’s no need to remember keys or a proxy card when leaving for work in the morning. All you have to do is grab your phone and voila—you can gain access to facilities or documents located on the cloud.

State-of-the-art smart readers are compatible with any access control system and can read both smartphone credentials and conventional smartcards.
By implementing mobile app access control, employers save costs and time associated with physical printing and distribution of identity badges or buying biometric readers. As authentication moves to the digital realm, many of these processes can be done online.
Advantages of mobile access control over other forms of access control #
- You can use a smartphone, a tablet, or a wristband as a single identifying technology for physical access control with multiple access rights (i.e., a parking lot, an office, or an IT system).
- There is no need to carry a proxy card or a fob with you.
- It enables biometric authentication.
- It is encrypted technology so it ensures a higher level of security.
- It can be used with traditional access control to ensure an extra level of protection.
All in all, the adoption of advanced mobile access control gives both employers and employees many valuable advantages and signifies a new era in access control technology.
Introducing Kisi mobile access control #
Kisi is the highest-rated app for mobile access control on both Apple’s and Google’s app stores. Our solution also has glowing reviews on industry software review websites like Capterra and G2. Thousands of people use Kisi mobile access to access spaces safely every day.
How Kisi works #
- Kisi's mobile access credentials are built for security and exceptional user experience: There is no need for users to pair or download credentials. Upon login, everything is ready to use, just like mobile banking.
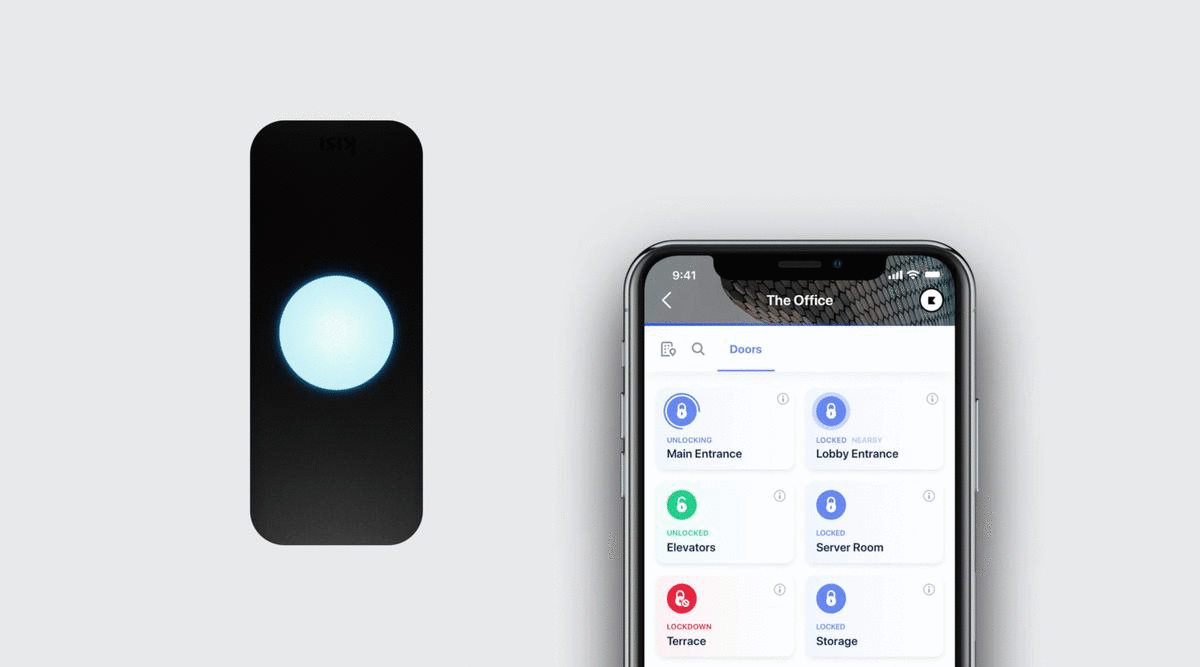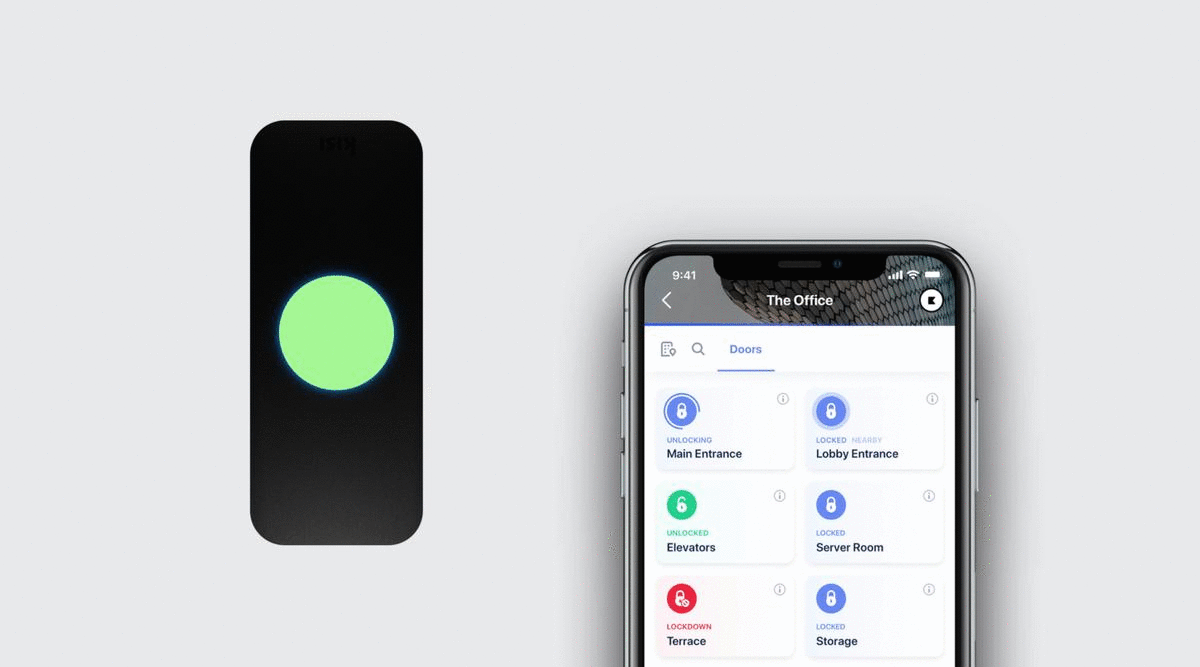
- When the authorized user approaches the door, they can hold their phone to the wall reader and, without even opening the App, the unlock signal is sent. For the user, it behaves exactly the same way as a keycard.
- Once the unlock request has been verified by the cloud server, the reader flashes green, notifying the user that the door has unlocked. If the door does not unlock, the reader flashes red.
- Once the user walks through the door, the unlock event from the access control reader is recorded along with the door opening event.
Some of the benefits of Kisi's mobile solution #
- Use of BYOD smart devices
- Latest technologies are available on most modern phones
- Self-governance and control by end-user
- Future proof technology
- In-sync with other software systems
Common questions about Kisi's mobile access control #
Does the user’s phone have to be connected to WiFi?
No, their phone just needs any type of internet connectivity if it is configured as a mobile-only unlock. If there is a reader that can read secure and encrypted phone communications, like the Kisi Reader Pro, in some cases, no internet connectivity is required.
Does the user have to pair the phone with the reader?
There is no pairing required; it works instantly. The pairing process you might be used to from your home Bluetooth speaker is not the case with the Kisi access control reader. All you need is to have Bluetooth turned on—then Kisi works its magic.
Which phones are compatible?
Most people use iPhones or Androids to connect with Kisi readers. Some people choose to use link access, should they opt to use a different smartphone platform such as Linux or Blackberry.
Which smartwatches are compatible?
With Kisi, users can also unlock doors with their Apple Watch, without the need to reach for their phone or key card.
How long does it take for the door to unlock?
It's typically faster than you can reach the door handle. We require the user to hold the phone just like a keycard to the reader, and from there, it's a matter of milliseconds until the door unlocks.
What if the system is offline?
Kisi supports an "offline functionality" that allows users to unlock the door with their phone even when their workplace internet connection is down. The cellular signal on your phone is still required, but you won't have to worry about any potential downtime of your network.
Are you interested in installing a mobile access control solution? Get a quote from us today.

