Organizations today have to contend with a variety of security concerns that exist both in the physical and digital space. The flow of information and access is more important to consider than ever, leading many to turn to more technologically advanced systems to ensure total coverage.
The type of access control that an organization selects needs to properly address concerns around the protection of physical space and information, as well as adhere to strict budgets. A system that is able to meet these criteria is an IP-based access control system, which offers multiple solutions to accommodate security at scale. In this article, we’ll explain the IP-based access control systems and explore the benefits of these setups.
IP-based access control systems #
The term access control (AC) refers to the system of selective restriction of access to certain information or place.
IP-based access control is a common solution in the security industry because of its efficiency and convenience. This type of access control has also become fairly easy to implement in the workplace because it only requires the proper hardware and an internet connection.
A few aspects of this system along with some of the benefits it offers will be discussed below.
An introduction to IP-based access control systems #
An IP-based access control system involves an electronic access controller that is specifically designed for controlling the entry and exit to and from a restricted area as well as for precisely identifying the users.
A controller of this kind is capable of supporting multiple (up to 4) basic access control readers. These readers are also known as non-intelligent readers, as they are only capable of reading the card number or PIN of an individual and sending it to the main server via Ethernet. In most cases, the Wiegand protocol is used for transmitting data.
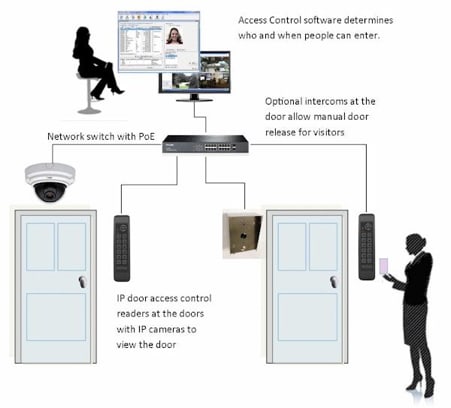
Differences between IP based and traditional access control systems #
In terms of building architecture and working procedure, these two access control systems have a few key differences. Some of these include:
- Unlike traditional access control, IP-based systems are directly connected to the LAN/WAN connection, and as a result, they can keep track of all input and output data necessary for controlling entry and exit, as well as door inputs and locks.
- Traditional access control system is incapable of functioning properly without the presence of a terminal server, whereas an IP-based access control system has its own onboard network interface that assists in independent functioning.
Types of IP access #
An IP access control system can implement more than one type of IP access. They are:
- Embedded IP access: This type of IP access can operate on a single site and the door count is usually low. Embedded IP access stores the important data regarding credentials and PIN numbers on the control panel which is directly connected with the browser. Embedded IP access based control systems are used in myriads of business sectors because it is relatively inexpensive and fairly easy to install and operate.
- Server-based IP access: The server-based IP access is capable of handling multiple websites simultaneously and the door count is much higher than the embedded IP access. Server-based IP stores all the necessary data on the server that consists of multiple control panels.
- Hosted IP access: Hosted IP access system is the most sophisticated system that can operate thousands of websites. Hosted IP consists of a highly secured data center with redundant backups and audited information security. In this case, the browser links to the web application containing several control panels.
Applications of IP based access control system #
Nowadays, this specific access control system has several applications in corporate sectors and the security industry. Some of them are:
- Biometric access control system: Biometric access control is often the chosen solution for the identification of employees in an office, as well as the applicants for a competitive exam. In this system, usually, a fingerprint is used for identification in high-security areas. In corporate sectors, biometric data is used to keep track of the employees’ attendance and calculation of payroll, whereas, in the case of applications, biometric is used to prevent malfeasances like forgery or identity theft.

- Proximity access control system: The proximity access control system is widely used in banks and corporate areas to ensure the safety of the surrounding environment. There are over 50 kinds of proximity access control systems available in the market that can be operated quite easily by implementing an IP-based access controller.
- Door access control system: IP-based access door closing and opening system is an extremely efficient as well as affordable security system. In this system, the door comes with an electromagnetic lock that can be controlled by an IP-based server for allowing the entrance and exit of certain individuals. Because of the simplicity of this system, the installation of door access control is also easier and relatively inexpensive. Nowadays, magnetic door locks with uninterrupted power supply are also used in airports, homes, offices, and data centers.
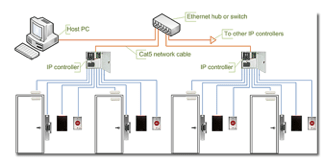
Reasons to use IP based access control systems #
This particular access system comes with numerous advantages. They can be described as :
- Easy installation: One of the principal reasons behind using this system is its simplicity. In this system, the existing network is used by the IP controllers to ensure the security of a certain restricted area. As a result, installing additional communication lines becomes irrelevant, allowing for the setup of this system to be much simpler and easier. Also, special knowledge around termination, troubleshooting, and grounding of RS-485 communication lines is not required for installing an IP-based access control system.
- Flexibility: This access control system offers immense flexibility as there is no limit on the number of total IP-based access controllers. You can install multiple controllers within a single system and increase the security of necessary information in a single installation. This flexibility not only saves a significant amount of time, but a considerable amount of money in terms of installation costs as well.
- Accuracy and speed: An IP-based access control system is capable of sending information to the main control unit and is able to take decisions accordingly, at high speed. Also, with all the necessary information stored in the database, this security system works infallibly by not allowing a single individual in the restricted area with a proper access code. Also, this system is capable of keeping records in an organized manner so that issues like attendance or proper identity can be easily resolved.
Conclusion #
In an increasingly competitive world, physical security and data security are essential to maintaining facilities and intellectual property, and must be properly considered. With the implementation of new technologies, the security industry is constantly upgrading, meaning it is more important than ever to future-proof the systems you choose. Under the circumstances, IP-based access control has become crucial for both discretionary and mandatory access control systems with its efficacy and numerous beneficial features.

