⚠️Important Update: Nearly 80% of all keycards used within commercial facilities may be prone to hacking due to protocol vulnerabilities. Kisi’s mobile credentials and 128-bit AES encrypted passes and tags are designed to protect your business from such threats. Explore the different access methods and our suite of access control products.
How we copied key fobs and found vulnerabilities in keycards #
In this post you'll learn:
- How many RFID cards exist
- Copying access credentials with Flipper Zero
- Step-by-step instructions on how to copy your office 125khz access cards in less than 1 minute (including the tools you need)
- Another step-by-step guide on how the more advanced 13.56MHz cards can be copied (and, of course, which equipment you need)
Basically that means you’ll learn how to clone cards (NFC or RFID cloner) at your office desk!
The impact of RFID cards and RFID key fobs #
IDTechEx found that the RFID market was worth $12.8 billion in 2022. The NFC market, on the other hand, reached $23.1 billion in the same year.
This market sizing includes all the tags, readers, and software designed for RFID cards and RFID key fobs, including all form factors. The market is estimated to rise to $31.5 billion by 2031, with an expected CAGR of 10.2% from 2022 to 2031. The security industry has experienced a major overhaul with advances in technology.
For example, door security has evolved from simple pad locks and keys through RFID-enabled cards and fobs that can be swiped and triggered, to mobile credentials safely and conveniently kept in your Apple Wallet. All while using electric locks to open doors. The amazing technological advancement requires constant evolution and adaptation to defend against malicious users.
Any new technology, from the moment it is introduced to the general public, is vulnerable to manipulation and hacking by malicious users. A good example of this is RFID tags in 2013. At the time, RFID technology had spread like wildfire across many sectors — tech companies, hospitals, and more were using 125khz cards to access doors secured with electric locks.
Most were using the EM4100 protocol card (a type of 125khz card) or a CMOS IC-based card, which had the information about the tag or fob stored openly. Since these ICs had no encryption or authentication, they would broadcast their information as soon as a reader was nearby. This posed a huge security risk to companies dealing with sensitive information and products. Essentially, anyone with the right equipment could steal or replicate these cards and fobs, whether they were authorized or not.
How can you copy access cards? #
Previous posts on our blog explore how HID cards can be hacked and how the Wiegand protocol, used by HID readers, can be copied by HID card cloners. This post doesn’t go into as much technical depth but, rather, should be a fast and easy way for you to understand the card copying component.
Copying access credentials with the Flipper Zero #

HID readers are vulnerable to attacks and can be compromised in less than 60 seconds. Unfortunately, the keycards and fobs these readers use are even less secure. Someone with bad intent only needs to be close to your card for a moment, and they’ll be able to access your secured spaces.
The Flipper Zero is an easily concealable, small handheld device. It can copy RFID, NFC, Sub-GHz, and infrared signals. It has become renowned as a hacking multitool, exposing the weaknesses of outdated systems.
Take a look at the video below to see Flipper Zero in action.
Countless videos of this device have gone viral, showing it turning off TVs in restaurants and playing messages over PA systems. However, when it’s not limited to minor pranks, this device can be dangerous. As you can see in the video, it shows how obsolete most keycard and reader systems are within the access control space.
With less than a second of contact, the Flipper Zero can silently copy the credentials from a keycard. It even works through wallets, pockets, and wallets in pockets. Someone sitting next to you on the train could use it to read and copy your card without you ever knowing. The Flipper Zero can then mimic the card, unlocking any doors the card has privileges to.
The reader can’t distinguish between using the Flipper Zero and the original card. Wrongdoers can also use the Flipper to quickly write new cards, creating a duplicate keycard that they can inconspicuously use.

Relying on obsolete technology to keep your spaces and assets safe is a risk considering how quick and easy attacks are. Upgrading to a modern cloud-based system like Kisi can help protect you against these vulnerabilities, while enabling a more convenient access control experience.
How to copy 125khz cards — the old Way #
Some readers can easily read the ID of an existing 125khz EM4100 or a similar type of protocol chip and copy it to another card or fob. One of the first people to attack this security standard in 2013 was Francis Brown—managing partner at the security firm Bishop Fox. Brown set out to deliberately test the security standard and developed an Arduino-powered reader/writer that could copy existing 125khz tags and fobs.

It’s been over a decade since Brown developed his tool to hack into these systems, and plenty of companies have switched to a more secure, higher frequency standard. Still, many businesses have not updated and still use the 125khz EM4100 cards and fobs, making them very vulnerable to attacks.
How to copy 125khz cards with an RFID copier #
Here is how the “Handheld RFID Writer” (that you can easily purchase for less than $10) works:
- Turn on the device. Hold a compatible EM4100 card or fob to the side facing the hand grip and click the ‘Read’ button.
- The device will then beep if it succeeds. Replace the copied tag with an empty tag and press ‘Write’.
- The information stored on the original tag or fob will then be copied onto the new device.
Done! Don’t believe how easy it is? See for yourself in the video below.
Copying or cloning an access card or RFID key fob has been easy for years.
How to copy HID cards and get them on your phone #
People were curious about copying access credentials for a while. They’ve been asking questions like: “How can a mobile’s NFC be used as an HID proximity card (used at the doors of a corporate office)?“ and “Is the iPhone 6’s NFC transmitter capable of being used as a contactless card reader?”.
In the following segment, we’ll focus on your typical HID card, which works off 13.56 MHz and can be harder to copy.
Why are these cards more difficult to copy? #
Since the frequency is significantly higher, compared to the 125 KHz version, the amount of bits that can be sent per second is significantly higher. That means the data on the chip to be encrypted will be greater, rendering it more secure. Encrypted cards send out a signal that the reader reads to communicate with it. Unlike before, it no longer advertises all of its data. Instead, it only broadcasts data that is public—like its ID and name.
How can you copy them? #
To access sensitive information, you have to provide that sector of memory with the right key—otherwise, it will show up blank. Even though these cards are a lot more secure, once you know the encryption algorithm, you can decrypt them and access sensitive information. With that, people could also clone these cards relatively easily.

Since most smartphones have NFC, reading these cards and, in certain cases, cloning them is easy.
—(If you don’t want to order equipment, skip over this part and learn how to duplicate the card using a smartphone and an app)—
- Prepare to copy your HID cards—the tools you need. To get started, we need a few cheap components from Ebay—it’s sold under “NFC reader.” I got my NFC reader/writer on NewEgg, which lists it as a “NFC ACR122U RFID” reader/writer tool. It runs on Windows, Mac, and most Linux systems.
- Once you have the copy tool, you need a Windows-based computer. Install its drivers and start using it. You’ll also need a computer to run the software, and following this guide, you can hack Mifare Classic 1K Cards. Here’s the BlackHat Guide.
Hold on! I hope you didn’t order the NFC reader yet. Chances are, you can also do it with your phone.
Cloning Mifare NFC cards with a mobile phone #
Although the BlackHat guide worked well, it can be a bit frustrating to use since you have to get some components together and hack away at a guide for an hour or two to see some results.
Here’s how you can clone Mifare NFC Classic 1K Cards using an Android smartphone with NFC capabilities. That’s right. You can use your cell phone to compromise the security of a company if they are using these types of cards. For more info on RFID security system read our guide.
Download the “Mifare Classic Tool” for Android. Go to your settings and search for NFC. Make sure to enable it. Now we can start cloning cards that have never changed their default sector password.
How the app is used to copy the card #
The app comes with the default keys set by the manufacturer of NFC cards. You would not believe how many people never bother to change this. Tim Theeuwes has a great guide on how to clone NFC cards using your NFC-enabled smartphone. The following images are from his guide.

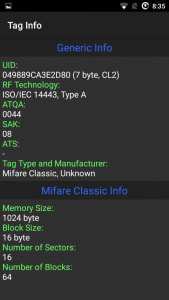
Hacking NFC via an app #
Once we have read the key or fob we want, we can store all of the information in a file. We can then use this information and write it back onto an empty card, essentially cloning the original card or fob. You can write individual sectors or all of them in the “Write Sector” portion of the app. The important sector to keep in mind is sector 0, as it contains the UID and manufacturer’s data. Basically, if you copy sector 0 to another fob, then you’ve made a copy.
The Kisi Reader Pro used the Mifare Desfire EV1 2K NFC cards. These have been some of the most secure NFC cards. They provide an added level of security to the already existing Mifare Desfire NFC cards.
Curious if you should use mobile credentials and 128-bit AES-encrypted NFC cards? Check this overview of our mobile access control system or get in touch with us. If you are more interested in how access systems work, download our free PDF guide.
Are you looking for secure access control? #
Request a quote on our website!






