Holding open a door for someone seems like a thoughtful and inconsequential event, but for some businesses, it can pose a serious security risk. A tailgating attack can create safety, financial, and reputational concerns for an organization, all without anyone realizing that it’s happening.
The good news is that your organization can take steps to make tailgating more difficult and less appealing to bad actors. With the right combination of technology and proactive strategies, you can prevent unauthorized individuals from entering your spaces. The first step to finding those solutions is understanding the fundamentals of what tailgating is and how it happens.
In this article, you’ll learn everything you need to know about tailgating attacks and what you can do to stop them.
What is tailgating? #
The word tailgating has long been used to describe a driver who follows another car too closely, but it has a separate meaning in the world of business security. Tailgating in that context refers to someone who closely follows another person to enter a building without using a key or authorization credentials. While this kind of tailgating doesn’t cause car accidents, it’s dangerous in its own way.
Types of tailgating #
Instances of tailgating don’t always look the same or pose the same level of risk for a business. Generally speaking, they fall into one of these categories:
- Malicious tailgating: Tailgating is malicious if a person knowingly exploits another person to enter a space they don’t have authorization to access. They usually do so to carry out questionable or illegal activity, such as property theft.
- Virtual tailgating: Tailgating can also occur in digital spaces if someone uses another person’s access credentials or network vulnerabilities to access confidential information. These attacks sometimes occur in tandem with malicious tailgating.
- Accidental tailgating: Many people tailgate without ill intentions, often because they forgot their key or ID card, have their hands full, or simply find it more convenient not to have to unlock a door. However, to minimize incidences of tailgating and keep your property secure, it’s best to make a general policy against tailgating and require every employee to scan their own credentials when entering your premises.
Understanding what types of tailgating your business is most likely to experience can help you set up the necessary safeguards to protect your employees, property, and data.
Distinguishing between tailgating and piggybacking #
Tailgating and piggybacking are closely related practices, so the terms are often used interchangeably. They both refer to individuals who follow someone else through a security checkpoint, but the method is slightly different.
In tailgating, the individual with access authorization is unaware that someone else is trying to enter. After they unlock the door, the tailgater sneaks in behind them. A person who is attempting to piggyback doesn’t try to hide their presence. Instead, they might strike up a conversation with the person entering to distract them or claim to be a delivery person who is dropping off a package.
Malicious tailgating and piggybacking are a form of social engineering where the attacker manipulates the target through deception or coercion. Through devious methods, they convince someone to take a seemingly harmless action—opening or holding the door—that could actually cause significant damage to the organization.
Although there are slight distinctions between them, both piggybacking and tailgating are a threat to businesses. Some video surveillance and access control solutions like Kisi effectively reduce the risk and give greater insight into who is entering your premises.

What is a tailgating attack? #
A piggybacking or tailgating attack is a malicious incident where an unauthorized individual attempts to gain access to a property for nefarious purposes. Unfortunately, these types of attacks are often difficult to recognize because they’re subtle. Rather than forcing open a door or breaking a window, the attackers take advantage of people’s carelessness, consideration, or politeness to get past security measures.
Who tailgates? #
A wide range of people with different motivations might attempt to tailgate and enter a restricted space. Some of the most common examples include:
- Former, disgruntled employees who want to seek revenge on their previous employers
- Vandals who want to damage or deface property
- Thieves who want to steal physical items or digital files
- Angry customers who feel they have been treated poorly by a business
Any one of these individuals could cause chaos, disruptions, and financial losses for an organization simply by following an authorized individual through a normally locked door.

Common tailgating and piggybacking methods #
Many strategies that people use to tailgate or piggyback center around human manipulation. For instance, it’s common courtesy to hold a door open for someone walking behind you, and attackers use this goodwill as an opportunity to gain access to a secured space. Because holding or opening a door for someone is a natural response for so many people, tailgating offers an easy way to get past typical barriers.
Tailgaters also use a number of other strategies to gain entry to a space, including:
- Posing as a delivery person, vendor, or contractor, potentially wearing a uniform or carrying a fake ID badge
- Carrying a heavy load of items so another person will feel compelled to open or hold the door
- Casually asking someone to hold the door while claiming or pretending to be an employee
- Staying out of sight or in a crowd of people until someone opens the door and then slipping in behind them
One of the most concerning aspects of all these tailgating methods is how difficult they are to track and detect. Without the correct tools, technology, and training, businesses leave themselves open to frequent tailgating.
Is tailgating illegal? #
Local laws ultimately determine whether tailgating is legal in your jurisdiction. In many places, a person who knowingly enters a location without authorization through tailgating is guilty of trespassing. This is a crime with potentially serious penalties, including jail time.
The legality of tailgating also depends on the intention and the outcome. For example, if an employee accidentally follows a coworker into their building without scanning their credentials, they’re probably not breaking the law because they’re authorized to be there.
On the other hand, imagine that someone tailgates behind a business employee and enters a building that they’re not authorized to access. Once inside, they use a company computer to access files and install malware. Because these actions are malicious and intentional, they’re likely also criminal.

Possible consequences of tailgating attacks #
While the act of tailgating itself might not seem that significant, what comes after can have a major impact on a business. Even if the individual is ultimately asked to leave, a lot can happen in the short time that they’re on the property, including:
- Committing a data breach
- Stealing money or items
- Damaging or destroying company property
- Acting violently and causing physical harm to others
- Accessing private documents
- Stealing hardware
- Infecting an unlocked computer with malware
- Launching a cyberattack on the company to steal confidential data
These crimes are particularly troubling because tracing their origins and locating a suspect is much more difficult if the person gained entry through tailgating. People often don’t notice or remember who entered a door behind them, and many security systems don’t alert you if someone tailgates.
Security measures to prevent tailgating and piggybacking #
Tailgating is widespread, affecting businesses of all sizes and across multiple industries, but that doesn’t mean your organization will inevitably suffer from an attack. With the right approach to security, you can significantly reduce the chances that tailgating and piggybacking will occur.
Preventative strategies and best practices #
Your business can take many steps to prevent and minimize tailgating attacks. First and foremost, it’s vital to provide comprehensive employee training that addresses all aspects of tailgating. Emphasize to staff the importance of closing doors behind them, explain how they can verify whether someone is authorized to access your property and tell them what to do if they find themselves in a situation where they suspect someone is trying to tailgate.
In addition to preparing your employees to encounter this kind of situation, you can also add security barriers to make it more difficult for attackers to enter. For many buildings, this means ensuring you secure spaces with a modern access control system. However, depending on the size and structure of your space, you might also use security turnstiles to better control the flow of foot traffic.
Another option is hiring skilled security personnel who understand what tailgating looks like and how to react if it occurs. For many businesses, however, employing security professionals around the clock is impractical and unaffordable. That’s why complementing your other security measures with technology is so critical.
Tech solutions for tailgating security #
Tailgating is an increasingly common occurrence for businesses all over the world. In one survey, around one-third of businesses said that they believed it was very likely that a security breach could happen due to tailgating at their facility, and another 39% said it was somewhat likely.
What’s most worrying, however, is the fact that nearly 75% of respondents said that they’re not currently tracking tailgating occurrences. Technology is the answer that these and all other businesses should be seeking to address their tailgating concerns. For instance, installing video surveillance systems with security cameras allows you to more closely monitor who is entering your premises and find evidence of tailgating if a crime occurs.
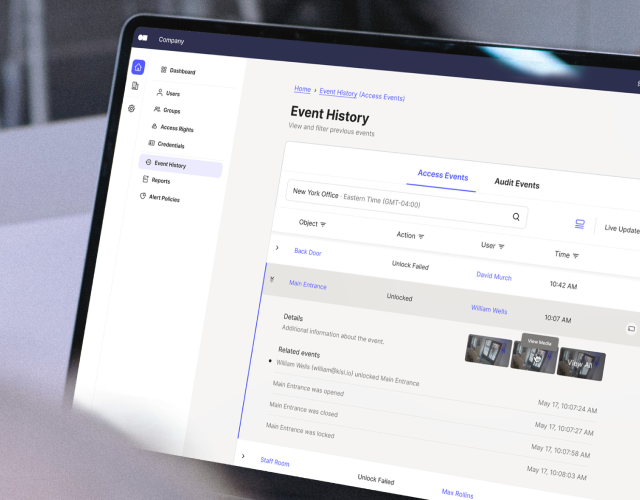
Most important to your efforts to curb tailgating is connecting your video surveillance to a high-quality access control system like Kisi. With access control, you can grant authorization to employees, visitors, guests, and contractors through a digital dashboard. You’ll also have varied access method options, including fobs, badges, and smartphones, so you can customize your access control to your business’s specific needs and preferences.
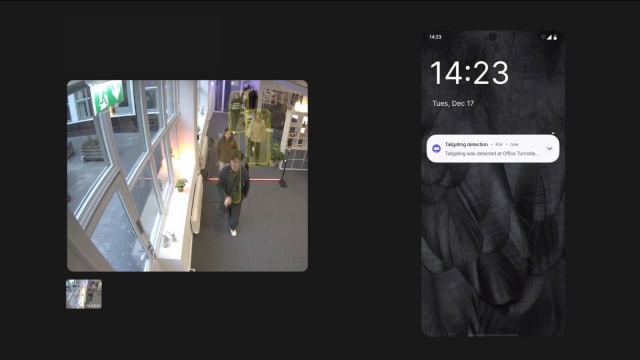
With Kisi, you can also set alerts to notify you if something suspicious occurs at your property. Door held open alerts are especially valuable when it comes to tailgating and piggybacking because they let you know if an employee might be allowing another person to enter without presenting their credentials.
Better yet, when you integrate your access control system with video surveillance you get a cohesive solution that addresses tailgating from every angle. For instance, you can identify and alert administrators to unauthorized entry attempts where an individual follows an authorized person through a secured door by connecting Kisi with Cisco Meraki, VIVOTEK VORTEX, and shortly SPOT AI.
Put an end to tailgating with Kisi #
Tailgating is a seemingly minor incident with a potentially major impact. When people enter a building without authorization, they can gain access to confidential customer data and proprietary documents. They can also wreak havoc on your network with malware, put employees in physical danger, and steal or damage your property.
To stop tailgaters in their tracks, you need a reliable security system. Kisi is a future-proof solution that offers remote access, straightforward management, and system alerts connected to your video cameras so you can maintain full control over who enters and exits your spaces. Reach out to get a free demo and learn how Kisi can help protect your business from tailgating attacks.