The surging crime rates reflect the increased security threats all types of facilities face. News outlets are filled with gripping headlines of smash-and-grab robberies and cargo heists. The majority (60.5%) of the almost 9 million offenses reported in the FBI's 2020 report were crimes against property.
Retail facilities experienced an average shrink rate of 1.4% representing $94.5 billion in losses in 2021. Retailers attributed the greatest portion of shrink to external theft, including organized retail crime, closely followed by internal (employee) theft.
$223 million was stolen across all cargo theft events in 2022, with distribution facilities and warehouses being the top targeted locations, according to CargoNet.

The various facilities involve unique security risks. Still, external and internal data and property theft are common security issues for all facilities.
The patterns and security threats are often similar across facilities, like employees bringing visitors to work without following security procedures or former employees holding relevant access credentials.
What is facility security? #
Facility security encompasses the measures and practices implemented to protect physical facilities, assets, and people from security risks, like unauthorized access, accidents, and potential threats. It requires some initial investment but saves you money and trouble in the long run.
Safety starts from the perimeter. Ensure that your space is secure even before people enter it. One example is making sure that your parking lot has barriers that allow access to members only. For extra protection, gates that regulate access, video surveillance, and good lighting are recommended.
Reliable access control at all access points you want secured is also essential to the physical security of your space. Cloud-based access control can serve as authentication, identification, and data analytics tool that also helps mitigate potential incidents. Integrated with the video and alarm system, it will protect the space from the most common security threats, like external and internal theft.
Modern access control systems like Kisi also complement your digital security measures. By physically protecting the facility, you decrease the chances of data theft incidents. For instance, installing an access reader in the server room, allowing only the individuals who really need access to the room to enter it, will minimize the chances of internal data breaches.
Cloud-based access control solutions also provide regular over-the-air software updates ensuring your system is up-to-date and protected against common cyber attacks.

Components of a comprehensive facility security plan #
- Procedure and equipment
- Attack and threat assessment
- Security countermeasures
- Audits and critical system checklist
Personnel and procedure #
There are various ways to improve your facility’s security, including the utilization of personnel, facility layout, equipment, and technology mechanism. Personnel includes individuals who visit and work within the facility, and facility security officers.
Every individual who enters the facility should be designated to a specific access group based on the principle of least privilege. They should be briefed and trained on the facility's security procedures.
The briefing, training, and vetting should be adjusted depending on the level of clearance and access. For example, the facility security officers you screen to hire should undergo several checks. These can include the potential officer’s financial and credit history, family and domestic history, criminal and police records, and a drug test.

Security officers are not the only ones that should receive extensive checks and tests. Most facilities are busy spaces allowing different kinds of groups like employees, contractors, and vendors to access the area.
Given the various visitors, changing personnel, and high turnover, management and security officers should anticipate a higher need for security equipment and protocol to prevent unauthorized access.
Employ a multi-layered approach to fortify your facility’s defenses against unauthorized access, theft, vandalism, and potential security breaches. If there are several security-sensitive areas and access groups, ensure the placement and security equipment reflect that.
For example, the physical space of heavily restricted areas should be isolated from less sensitive areas. The equipment for maximum security facility areas should include access readers with two-factor authentication (2FA) and intrusion detection, surveillance, detection equipment, alarms, and so on.
When evaluating the facility’s layout for security risks, take into account the positioning of equipment and spaces. To ensure everything is on track, conduct a physical security risk analysis. Read our guide to physical security assessments to learn more.
Audits and critical system checklist #
Audits are objective inspections to evaluate prospective threats that could impede the security of a facility and its operations. Audits serve to critically assess the effectiveness of the facility security program and its applications.
By identifying possible points of unauthorized access and disruptive events, it can also provide recommendations as well as a response plan to improve the facility's security. Security officers and facility managers can aid the audits by providing facility-specific technical details.
If possible, security checks should be included during the construction of the site. As a result, the facility layout will be better suited to your facility, and most risks or threats during the construction period will be neutralized.

During a typical facility security audit the auditor will examine the facility’s perimeter, access points and equipment, utilities, structure, envelope, interior, access, elevators, fire control, HVAC, electrical, and communications.
When investigating the facility’s utilities focus on the evacuation plan and continuous-operations needs in the event of a power shortage or evacuation, like emergency generators and backup water supply.
Inspect the security of physical barriers and perimeter protection to assess the facility’s structure. When assessing the envelope, evaluate the integrity of blast-resistant walls, bullet-proof glass, designated pressure-release panels, and access points.
Make sure your access control hardware and software is maintained. All access hardware, like access panels, readers, doors, and locks, should be functional.
The software should cater to all facility security needs and be regularly maintained to follow compliance protocols and guard against possible physical and cyber attacks.

Using cloud-based access solutions like Kisi will ensure all users have their unique access needs covered, while the over-the-air updates allow software maintenance without any costs on your end.
Regardless of the ease of use, consider the personnel and the application of security training, monitoring, and security systems for employees, visitors, contractors, and security officers.
Assess the vehicle transportation to the facility, fire control, HVAC, and electrical components to identify any security hazards and code violations that would endanger the individuals and the facility’s safety.
To assess the communication aspect of the facility security, test the facility’s automation systems and integration to public and emergency communications.
After completing the facility security audit, communicate the results and response to the proper officers and individuals. This communication is key to updating the facility’s security measures and preventing future threats.
You can use our workplace security audit checklist to get started with your facility security plan.
Attack and threat assessment #
Depending on the purpose and contents of the facility, different possible attacks and threats may arise. Threats to the facility occur at physical and digital access points, like doors, gates, hardware devices, and software applications where security can be breached.
Physical access points can be controlled through access control solutions, integrated with closed-circuit television (CCTV) cameras and sensors, and by employing security officers at entrances. Access control equipment aids in both detecting and neutralizing threats.

The risks are diverse with digital access points such as network servers, switches, websites, mobile apps, code, system access points, cloud storage, email applications, databases, and file storage systems.
Enforcing strong authentication, updating software, utilizing firewalls, and implementing secure remote access and user access controls, are some of the basics to protect your facility’s digital access points. Complement these with conducting security training, employing network segmentation, and maintaining continuous monitoring and assessments.
The best way to neutralize possible threats once the security system is set up is to periodically go through a facility maintenance checklist.
Security countermeasures #
To tackle prospective and current threats, many companies integrate cloud-based and mobile technology into their security. The shift to hybrid work and the need for enhanced productivity and convenience necessitate significant changes in facility security.
To accommodate and protect both on-site and remote employees, organizations adapt their security measures by implementing cloud-based security solutions, virtual private networks (VPNs), and multifactor authentication (MFA).
The shift to the cloud also provides admins with more flexibility and the ability to remotely manage global spaces, automate tasks, and reduce operations costs.
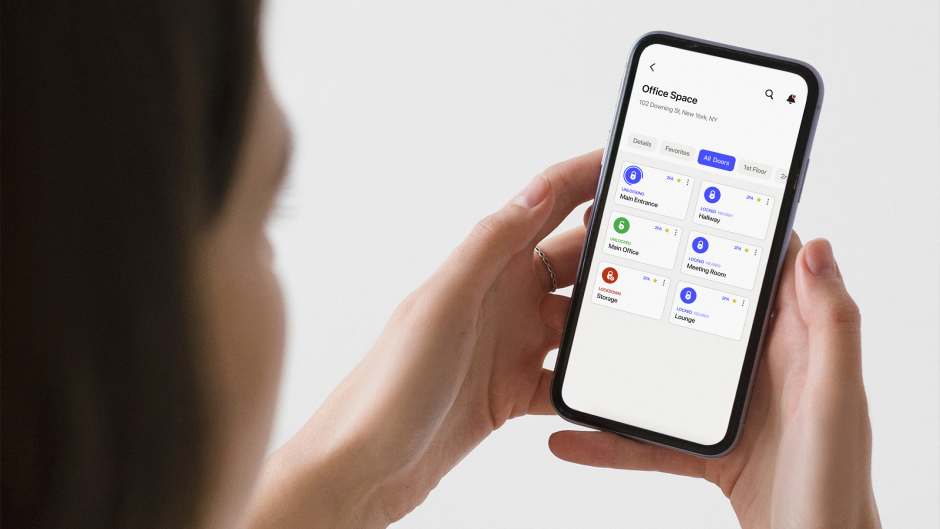
In addition to the cloud, technologies such as biometric authentication, the use of mobile credentials and digital wallets for contactless access, leveraging AI and ML for threat detection, have all improved security measures for facilities. Managers and designated officers should look towards including these tools as a means of heightening security, especially in more restricted areas.
Mobile credentials, unlike physical magnetic strip or proximity cards, are hard to replicate, and get stolen, misplaced, or lost. This allows facility users to use their mobile phones to unlock the doors they have access to.
Mobile access also improves data insights for seamless compliance audits, allowing easier monitoring of facility members, which is especially useful in an emergency or in the case of device theft.
With MFA, security becomes more organized and verified. Users that use mobile credentials can easily get identified through their mobile phone’s biometric inspection tool. This prevents data theft, impersonation, as well as credential loss. Modern companies quickly assimilate and implement mobile access across their facilities, to dramatically improve security and monitoring.

For an extra layer of security, integrate your access control with a video management system (VMS) that uses computer vision technologies to visualize objects and match behavior. The VMS is set to recognize certain patterns and behaviors, like tailgating, that can trigger an alarm or send an alert for security officers to investigate.
Modern facilities add cloud-based solutions like Kisi to enhance their facility’s security and access convenience. The real-time alerts and data integrate seamlessly to reach all areas that are monitored through CCTV cameras. The automation possibilities reduce the need for manned security, saving on operation costs.
Technology is continuously evolving to find ways to improve, automate, and link various security tools together. Implementing a future-proof system like Kisi enables you to keep up with the trends and find the migration path that best suits your needs.

