Originally introduced in a collaboration by Intel, Ericsson, and Nokia in 1994, Bluetooth changed the game for close-range communication. At the time, the internet existed and was booming, but there was still not a reliable and unified method for communicating over a local network at short distances that didn’t require internet connectivity. So these three industry leaders got together with the goal of creating a common standard for such communications. The plethora of use cases need not be rehashed here—these days, pretty much every electronic appliance you have is equipped with Bluetooth and uses it to interact with other appliances and, crucially, with your smartphone. In this article we want to explain more how Bluetooth works in general and with access control.
What is Bluetooth?
… and where does the name come from?
Before diving into the technical explanation, let’s take a brief look at history. Recognize this handsome fellow?

You’re looking at the one and only King Harald Bluetooth, the viking leader who was famous for two things: Unifying Scandinavia for the first time in 958 C.E., and having a prominent dead tooth (which was, aptly, a blue-grey color). Allegedly, one of the heads of the collaboration that created the technology is said to have proposed the placeholder (temporary) name Bluetooth because, “King Harald Bluetooth was famous for uniting Scandinavia just as we intend to unite the PC and cellular industries with a short-range wireless link." The name stuck, whether or not the quote is true, and they created the famous Bluetooth symbol as a combination of the old Norse runes for H and B (King Bluetooth’s initials).
Tech Specifications of Bluetooth
Now onto the technology. Bluetooth, as mentioned, is a short range wireless technology. It operates in the ISM band of radio waves (a range of frequencies), which is an international standard reserved for industrial, science and medical applications. The ISM band is a free band. This means that it does not require lengthy licensing procedures and fees—anyone is free to develop applications that broadcast along it.
This is crucial to the success of Bluetooth; you can easily imagine that if the technology were proprietary, or expensive, it would be in much narrower circulation than it is today. It operates in two primary frequency ranges within the radio wave band—2400 to 2483.5 MHz and 2402 to 2480 MHz—via the frequency hopping spread spectrum radio interface technology.
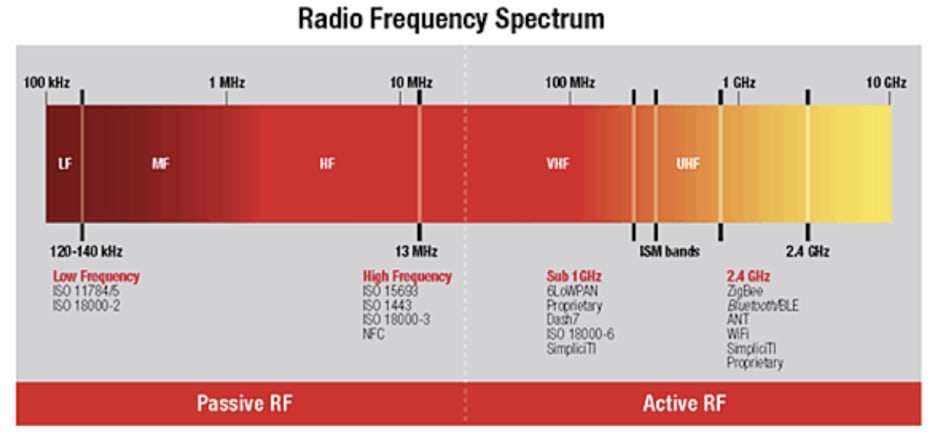
Bluetooth transmission frequency band is divided into 79 Bluetooth channels to transmit the data packet. The latest version of this communication technology known as Bluetooth Low Energy or BLE accommodates 40 channels because it uses 2 MHz spacing guard band, meaning it distinguishes bands by adding wider separation between them, resulting in less noise and crisper, more accurate signals (more on this new standard shortly).
The upshot of this is that Bluetooth uses frequencies that don’t interfere with most household objects, meaning that they can freely roam (as opposed to visible light), and the signals are strong enough to carry significant-sized data packets (more on this later).
Bluetooth Low Energy Standard
The newest and most sophisticated standard of Bluetooth technology is, as mentioned, Bluetooth Low Energy (BLE). BLE was developed by the Bluetooth Special Interest Group (BSIG) for high energy efficiency and performance. This technology is commonly marketed as Bluetooth Smart technology in the marketplace. Essentially, BLE represents a clever innovation that can transmit greater quantities of data and at similar ranges, but over fewer channels, meaning that it consumes less energy.
Thus, BLE devices can operate for many months, even years, on a single battery or charge. The result is that BLE technology is very suitable for the internet of things (IoT), where connectivity is everything and users want reliability without having to go around changing batteries every week. BLE technology can operate with a maximum speed of 50 Mbits/s up to an effective distance of 800ft (240 meters).
What are the applications of Bluetooth?
Now that we have some background and an idea of what’s going on behind the scenes, how is this technology practically implemented, and why did it proliferate as widely as it did?
In Bluetooth tech, there is generally one main machine that controls the signal, and pings its associated machines for data and general synchronization. This main controlling machine is the master, and the associated devices are, somewhat anachronistically and thoughtlessly named, the slaves. Here is a general diagram of that interaction.
The master will create what is called a Personal Area Network (PAN) in its vicinity (as denoted by the “personal area” name), and co-opt any other devices in said area as its temporary slaves. It will then send and request data from the slaves as needed through its dedicated Bluetooth antenna, and in turn they will transmit their data over Bluetooth to the master.
Which device is the master and which is the slave is a fluid process: It merely depends on which device is creating the PAN and requesting data from the other devices. As such, there can be nested master/slave relationships, and the roles can be flipped ad hoc over time.
Multimedia Transfer
Perhaps the most famous application of BLE technology is multimedia transfer—any time you link your phone to wireless earbuds, or your desktop to a wireless keyboard, you are using Bluetooth to accomplish a wireless multimedia transfer of data (be it audio, visual, or textual data).
The carrying capacity of Bluetooth technology is one of the main reasons it has become so widespread: Text files (as with a keyboard) are mere kilobytes of data, but files like videos, which can still be transmitted via Bluetooth, represent gigabytes of data. Many WiFi networks still struggle and present pixelated/grainy screens; however Bluetooth handles such transfers with ease, provided that the devices are within range.
Smart Home Automation
An increasing trend today is smart home connectivity: With the proliferation of smart home hubs like Amazon Alexa, Google Home, and Apple’s HomeKit, modern homeowners are connecting every possible device to the network, be it smoke detectors, smart doorbells, or even access control systems like Kisi. All these devices have to communicate with each other somehow and while they are all networked to WiFi, over the small distances of a home, they use Bluetooth—relying on its strength and the fact that it doesn’t shut down if the power shuts down.
The iBeacon
Being Apple, the company decided to develop its own protocol on top of BLE technology, and in line with the rest of their products, they dubbed it the iBeacon protocol. iBeacon runs within the iPhone and when it detects that there are other iBeacon-enabled devices nearby, it pings them, adding a layer of personal Apple encryption over the regular connection.
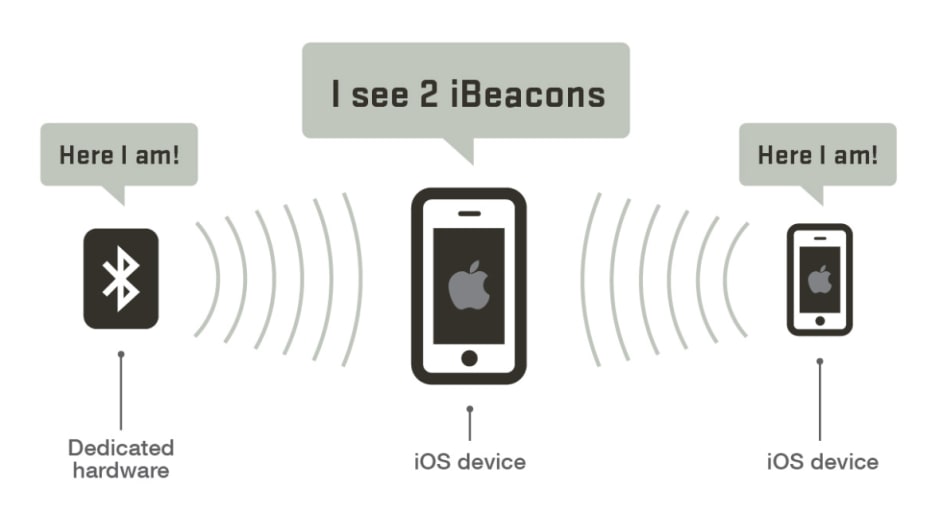
The introduction of the iBeacon protocol in 2013 was another important milestone in using Bluetooth technology in more access control and security-related applications. It can be extensively used in the applications pertaining to location finding, which subsequently will trigger a major potential of marketing services. Recently, iBeacon has been implemented in multiple BLE-enabled devices that can easily communicate with the mobile applications in their respective ranges over Bluetooth technology. The power consumption of iBeacon transmitter is very low and can operate for many months continuously on a small battery. Kisi’s own solution of BLE readers uses iBeacon tech, which allows us to transition nicely into the next section—Bluetooth in access control.
Bluetooth in Access Control
One of the coolest applications of Bluetooth technology, in Kisi’s unbiased opinion, is in physical access control. Gone are the days of the archaic and frequently lost keys and locks, gone are the days of inflated wallets with dozens of access cards, welcome to the days of the smartphone as an access credential itself!
BLE Door Readers
Much like its cousins Zigbee, ZWave and NFC, Bluetooth can be efficiently used as an effective access control technology.
There are large numbers of software applications available on the market that can be configured—commonly known as ‘profiling’—on Bluetooth-enabled mobile phones. They establish short range communication with Bluetooth-enabled proximity sensing devices. Other than those software applications, BLE can also be implemented in an autonomous Bluetooth access control system.
In a normal access control system, based on the iPhone, you’ll need a proximity reader enabled with Bluetooth signals. For a relevant example, check out the specs of Kisi Bluetooth-enabled reader. Usually, you will then need to install an iOS or Android application on your smartphone, and grant it access to the Bluetooth antenna to profile it for access control use. Then, when the smartphone is near the proximity reader, the application will communicate through its iBeacon with the reader and exchange the security key to authenticate and open the door lock.

Similarly, in an automated and networked house or office, your phone communicates with the centralized access controller, which controls the door locks in a networked environment. The security key is authenticated and the authorized door is opened through the signals from the main access controller.
There is usually also the option of interfacing with the door readers through the app itself. A good access control app will have a dashboard where you can scroll through your assigned locks and unlock them within app itself. This generally facilitates the process if you need to let someone else in or if, for some reason, the iBeacon signal is malfunctioning. This feature, in Kisi’s model, is available on both the iOS and Android app versions.
It’s important to note that there is, however, an imposed maximum range on this feature— known as BLE fencing. This is distinctly different from the limited range of, say, Kisi’s BLE “Tap To Unlock” function, which is active on iPhone. For Tap To Unlock, through sophisticated machine learning algorithms, Kisi’s BLE readers recognize when the iPhone is attempting a tap, and activate the reader when the tap is completed (and the iPhone is within a couple of inches of the reader).
The BLE fencing extends to the maximum BLE range of the reader, generally around 10 feet (barring any interfering metal obstacles). This means that as long as you’re within that range, you’ll be able to use the swipe to unlock feature in the Kisi mobile app.
Amongst the backdrop of changing lifestyle habits to doing everything on mobile, there is now a general push within the access control market to go from cards to mobile too. With unlocking doors from mobile becoming an ability people expect to have, it is poised to become the main method of unlocking doors in the next few years.
BLE Smart Locks
Another good example of Bluetooth in access control is a new generation of BLE-enabled smart locks that are able to interact directly with the phone to unlock doors. A good example is Allegion—it offers a range of BLE-enabled locks.

The best use-cases for BLE-locks are organisations looking for an access control security solution, given that these locks will be able to provide real-time communication and feedback. Among other benefits, this also means being able to grant or relinquish access immediately, and review real-time activity logs. Organisations with high traffic inflow and outflow will find such features most useful in streamlining their daily operations and strengthening their security.
As users will be required to swipe in-app to unlock, this also presents opportunities for any facility or workspace management apps looking to drive usage and engagement of their apps. By requiring users to unlock doors through their app, apps like Kisi’s iOS app will now become a daily necessity rather than a possibility.
Advantages of Bluetooth
Inter-Compatibility
If you’re familiar with modern contactless localized tech, you have likely heard of a new innovation known as NFC, or near-field communication, making waves. The solution is quite a clever bit of engineering. However, it’s by no means a general standard yet, and presents its own set of limitations. While the parent technology, RFID (radio frequency ID) has been around since the 80s (Bluetooth is a form of RFID, technically speaking), NFC in its current form was only introduced in 2002, and is not supported by such a wide swatch of appliances and devices—yet. Its range is rather limited (within inches), and its data transfer carrying capacity is more limited.
Bluetooth, however, has been the standard since 1994 and has a much deeper market adoption rate. As we’ve touched on, most contactless communication is done over Bluetooth and, quite frankly, if a wireless device isn’t Bluetooth-enabled these days you’re probably better off searching for alternatives.
Range
Another strength of Bluetooth devices is its range. Bluetooth devices are generally divided into three power classes, where the tech is essentially the same, but they draw different amounts of power from their source. The more power that’s drawn, the longer the range. Class 1 devices, which tend to draw a lot of power, can have a working range of up to 100 meters (300 feet), whereas BLE devices will fall into Class 3, and have a range limited to around 1 meter (3 feet) for the sake of conserving power.
With smart home appliances, which tend to be wired in, power usage isn’t actually an issue—they can have very long ranges, reaching into every corner of your house or space. This versatility in the tradeoff of power usage and range is a key advantage to Bluetooth tech.
There might be some confusion here, though, because the range of Bluetooth is inherently variable and not set: Some companies choose to set their BLE fence at two feet, some set it at 10 feet; essentially, there is no set standard.
Disadvantages of Bluetooth
Wake Up Time
A corollary of the power usage vs. range issue is that on devices, like iPhones, where battery consumption is front and center in everyone’s mind, Apple simply can’t afford to have the Bluetooth chip constantly broadcasting and attempting to connect. Even with the new BLE standard, this would sap too much battery, and force users to charge their phone more often.
As a result, they have designed the phone and their proprietary iBeacon tech so that the Bluetooth chip becomes dormant after a short period of inactivity, and only “wakes up” when prompted to do so by a detected iBeacon signal. While this does allow the phone to maintain its charge for a longer period, it means that there is a slight latency between when you expect your iPhone’s Bluetooth to work, and when the chip has actually woken up and transmitted a signal.
Distortion and Interference
Bluetooth has become such a popular technology because of the fact that it’s on a free band of radio frequency, but this does come at a cost: It shares the same band with many other technologies, most notably WiFi and microwaves. Having devices make use of both of these technologies in close proximity may cause distortion or interference with the signal.
Microwaves are a pretty straightforward case. They emit powerful radio wave signals (despite, as the name suggests, primarily emitting in the microwave range). Thus, if you attempt to use a Bluetooth connection near a microwave in active use, the signal may become garbled and distorted.
WiFi is a more subtle case. WiFi operates along radio bands, since it also transmits information through light signals. It transmits along a wider swatch than Bluetooth, however it does interfere with the Bluetooth 2.4 GHz band. This means that if you have strong WiFi and Bluetooth connections in close proximity, the signals could get jumbled together, resulting in what is generally called “static” (noisy interference). If this happens, try moving the WiFi receiver closer to the router, and the Bluetooth devices closer together. This will help reduce the interference.
Finally, there is the issue of multiple Bluetooth devices interfering with each other. They use the same frequency band, and will likely have similar antenna builds, so if you put two Bluetooth devices next to each other, they may amplify each others’ signal, but also become slightly distorted. Definitely something to keep in mind!
Concluding Thoughts
Access control has been increasing in sophistication in recent years, and its marriage with Bluetooth technology in mobile devices is perfect. Using Bluetooth with third-party controllers and readers reduces hardware costs and makes the unlocking experience much more enjoyable. With the advent of BLE technology on the market, this field has a bright future in the IoT industry.
Save time. Enhance security.
Modernize your access control with remote management and useful integrations.
Continue learning

